Risk analysis
The effort to understand a particular risk is called risk analysis. In risk analysis, we probe the depths of a single risk. It is an investigation of a risk that results in a rating and input for risk evaluation.
The effort to understand a particular risk is called risk analysis. In risk analysis, we probe the depths of a single risk. It is an investigation of a risk that results in a rating and input for risk evaluation.
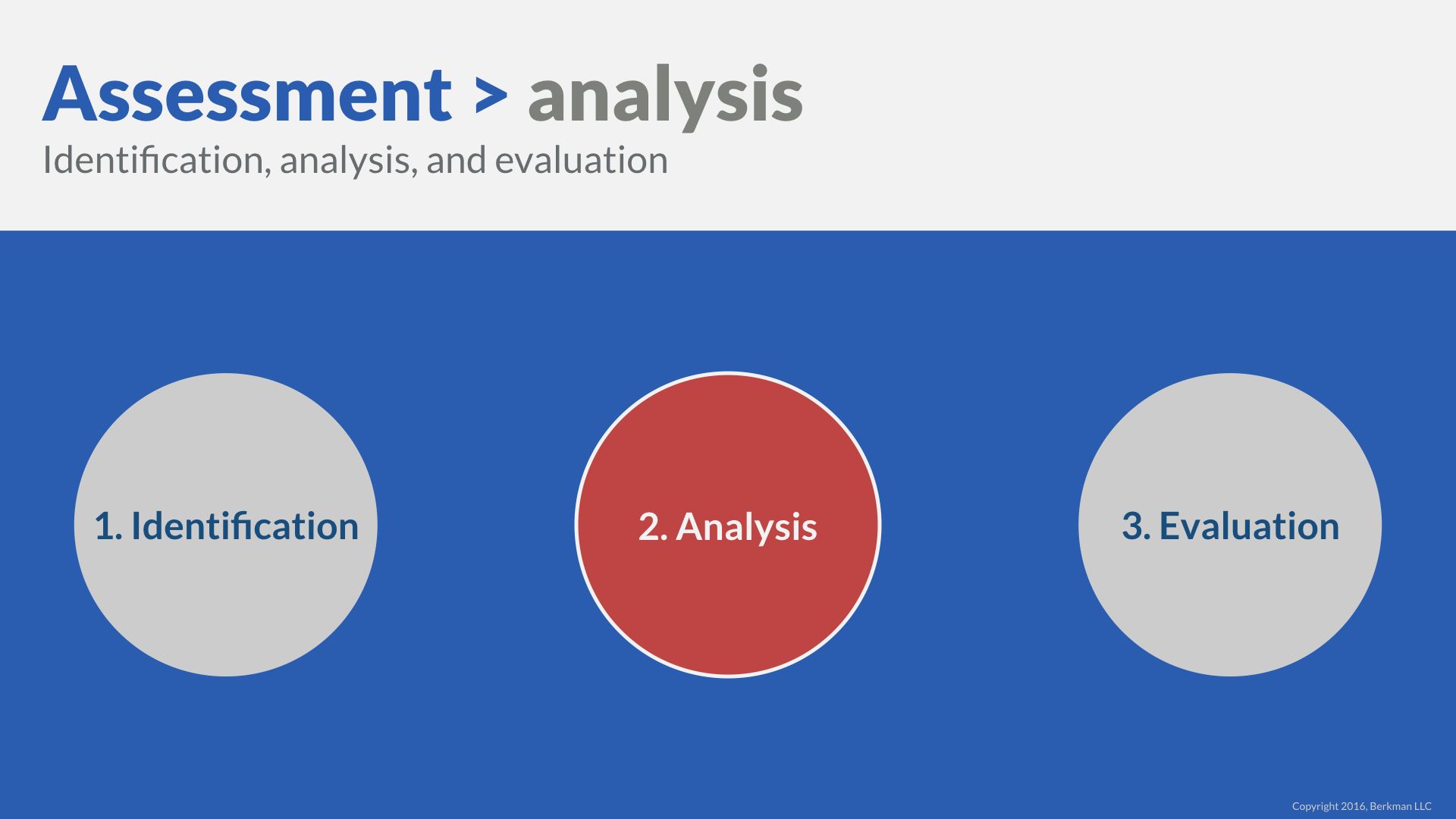
Risk analysis values depth over breadth.

Risk analysis refines the risk rating
In a risk analysis, we want to rate the likelihood and consequences of a risk event. Now you might ask, “But we did that during the risk identification?”
When we identified risks, our likelihood and consequence ratings were preliminary. We captured ratings in the spirit of breadth over depth. With risk analysis, we need to refine our estimates of likelihood and consequences. There is still room for uncertainly, which is inevitable.
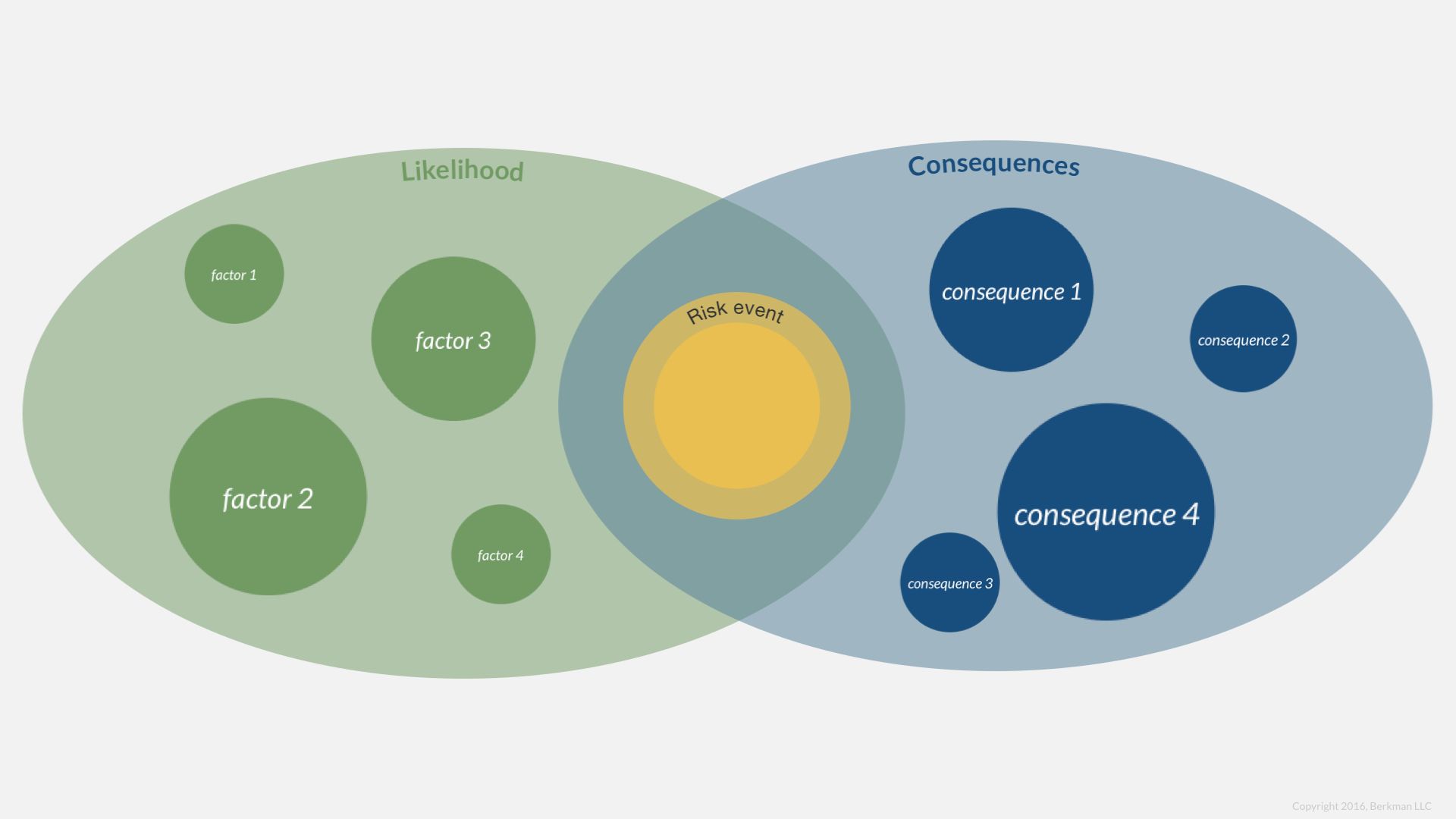
Up to this point we have looked a likelihood and consequences as a single rating plucked out of the air. We want to probe the factors that support a rating.
Likelihood
Let’s consider the factors that might make a legal risk more or less likely.
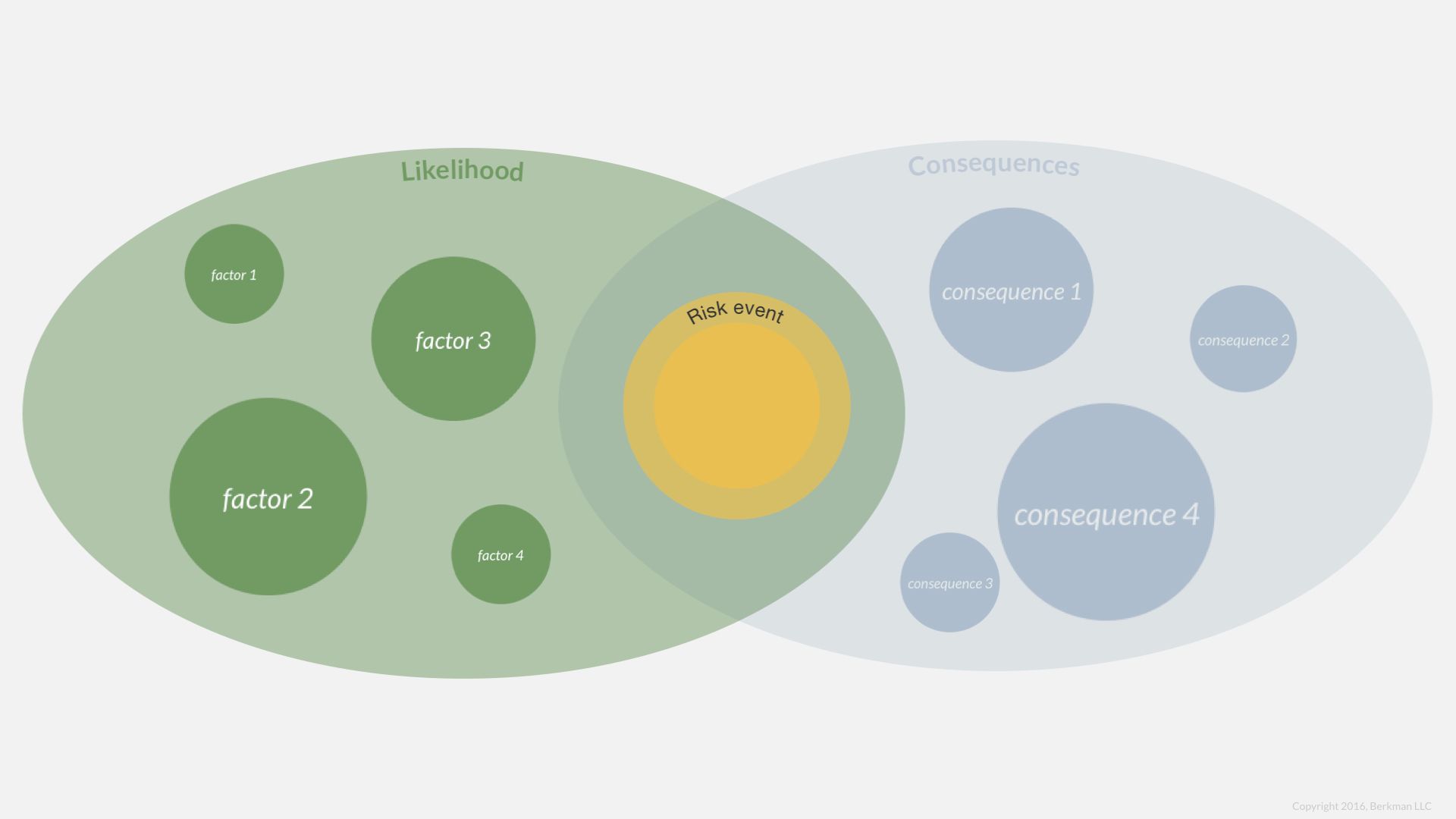
For example, what is the likelihood that the Federal Trade Commission (in the United States) will pursue an unfair and deceptive practices claim against our organization?
We might consider a few factors:
- To what degree is there a violation of the statute, if any?
- How many similar cases as the FTC pursued recently?
- Does a leadership change at the FTC influence the chances of a suit?
- Do we have any outstanding or prior issues with the agency?
- Are we continuing the practices?
- Has our conduct exacerbated or ameliorated the issue?
Notice that some of these questions aim to predict whether an agency will take action; other questions are about the merits of the violation.
The point is that we can evaluate disparate factors to form an opinion of a single likelihood rating.
Moreover, we can layer in the collaborative techniques to generate a list of factors and evaluate their importance of the likelihood rating.
Consequences
Likewise, we can deepen the understanding of consequences from a single risk event by considering relevant factors.
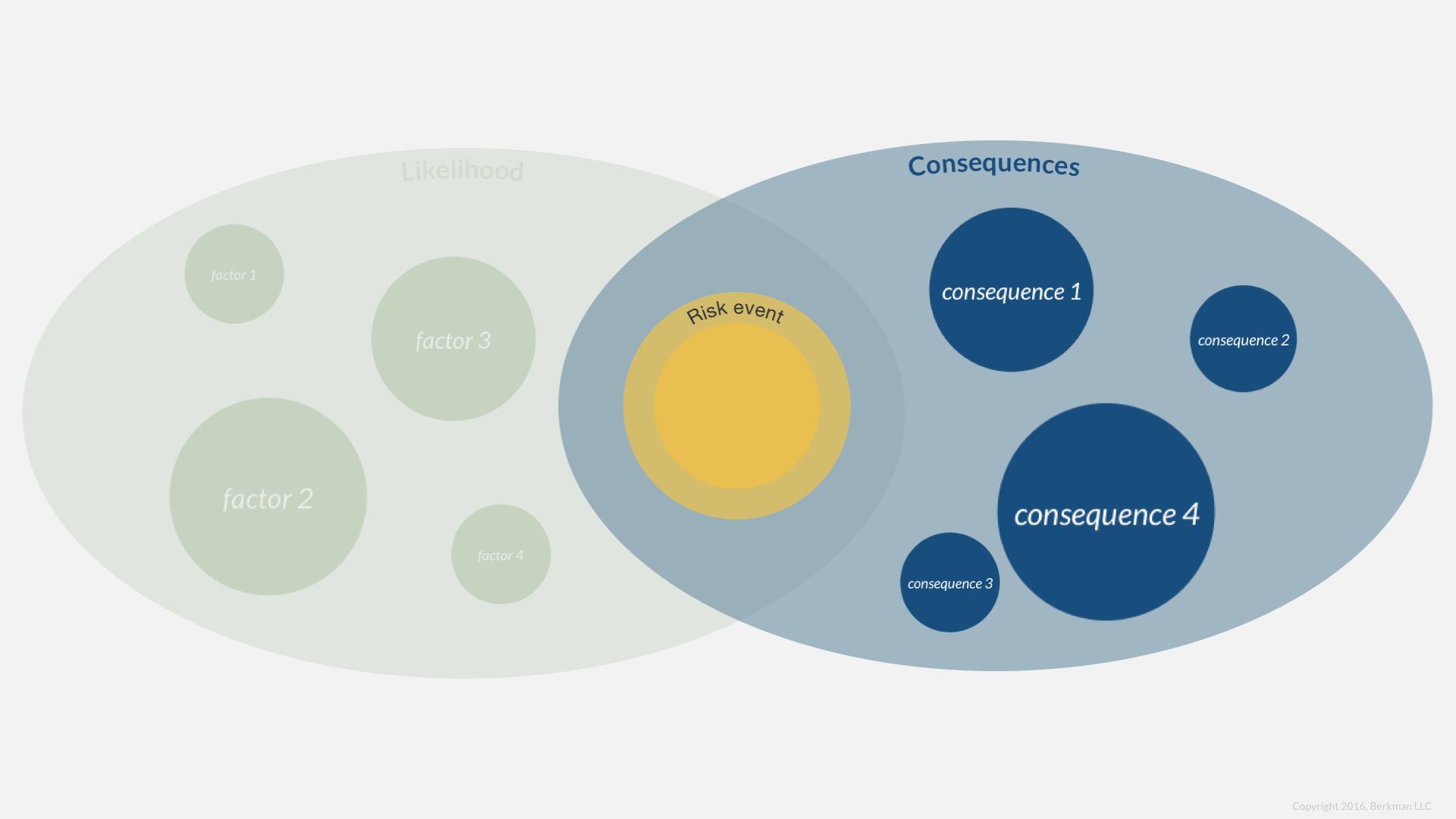
Consequences are often financial, even when they are imprecise. The consequences of product liability litigation, for example, are certainly financial. To measure those consequences, we might specify the following:
- The minimum compensatory damages available,
- The maximum compensatory damages available,
- The punitive damages claim available as a multiplier, range, or amount, or
- The availability of attorneys fees (this might also influence our likelihood rating).
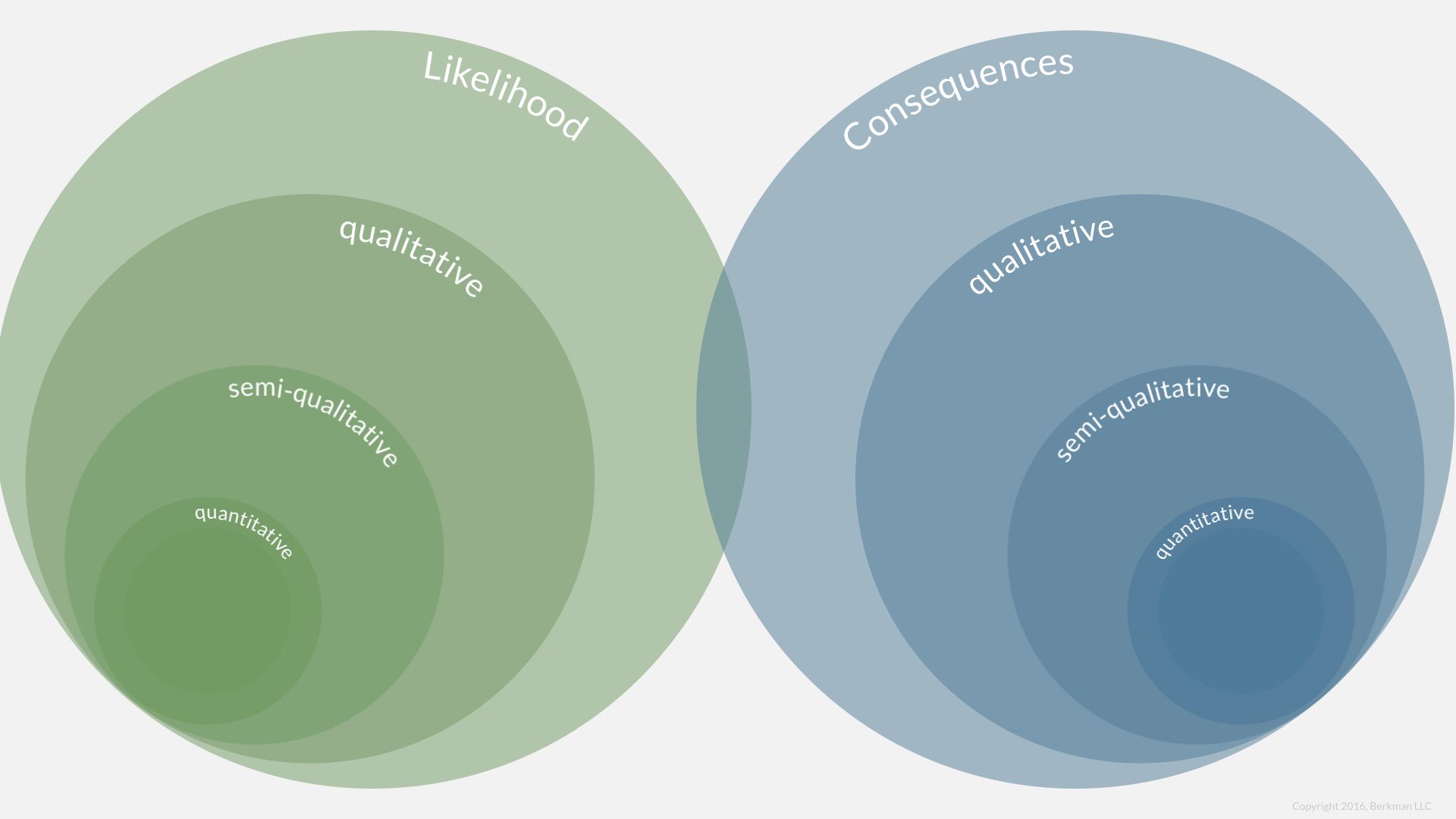
Techniques and data
When we consider factors for likelihood and consequences ratings, we can employ techniques tailored to the purpose. When quantitative data is available and relevant then we should use it. We should identify our data sources as evidence to support the rating whenever possible.
Risk controls
Once we have more ratings for likelihood and consequences with less uncertainty than during the initial risk identification, we look to our risk controls.
Some risk events are completely and utterly unexpected. In 2007, very few home builders in the United States thought to themselves, “I know, I should start worrying about a complete collapse of the US real estate lending market that would spill over and bring home construction almost to a halt.”
In many cases, however, we deal with “known unknowns” such as cyber security risk. We know there is a risk to our data, even though we might not know the likelihood or the consequences with precision. Based on this knowledges, organizations implement cybersecurity controls preemptively.
Controls might include firewalls, encrypted databases, secure transactions, limited access to sensitive data. A risk analysis need to consider the effectiveness of any preexisting controls.
A risk control is any process, policy, practice, or technology that modifies the likelihood or consequences of a risk event.
To use a contract risk example, consider a directive from the corporate counsel office that no sales agreement can include an indemnification clauses for data breaches. This is a reasonable provision to exclude from our contracts.
How effective is the memo about indemnification for data breaches at preventing the language from entering sales contracts?
It depends:
- Does a lawyer review each sales contract?
- Does a technology solution limit changes to contracts to prevent indemnification clauses?
- Was any process changed to implement the directive?
- Is there any review of existing contracts for indemnification clauses?
Answers to these questions will help us determine whether or risk control is effective or not.
Effectiveness means that the control reduced risk in a meaningful way. Our database encryption technology reduces likelihood to “unlikely.” The environmental accident insurance policy reduces the consequences of a spill to “material.”
The analysis should identify evidence that the solution works and we need to document the control with the results.